We are in Tokyo Cyber Security Meetup!

Challenges in DX and Cyber Security in Japan - Consento joined the panel discussion at TCSM#
We are delighted to announce that we joined in Tokyo Cyber Security Meetup (TCSM) as a co-host for their monthly meetup where we will be having interesting guests from Japanese business scene to share their expertise in security. TCSM is one of the biggest cyber security meetups in Japan led by Gino Bautista and Thomas Glucksmann, and their commitment to give something back to the local community is tremendous that moved us as well as an international startup bridging between Japan and Europe.
In our first Japanese meetup, we welcomed Mr.Shunji Koyanagi from SANS Institute and Mr. Keiichiro Nozaki from F5 Network. They gracefully shared their point of views on the current digital transformation demographic, and challenges that Japanese corporates are facing today.
Here are a few key take aways from the discussion;
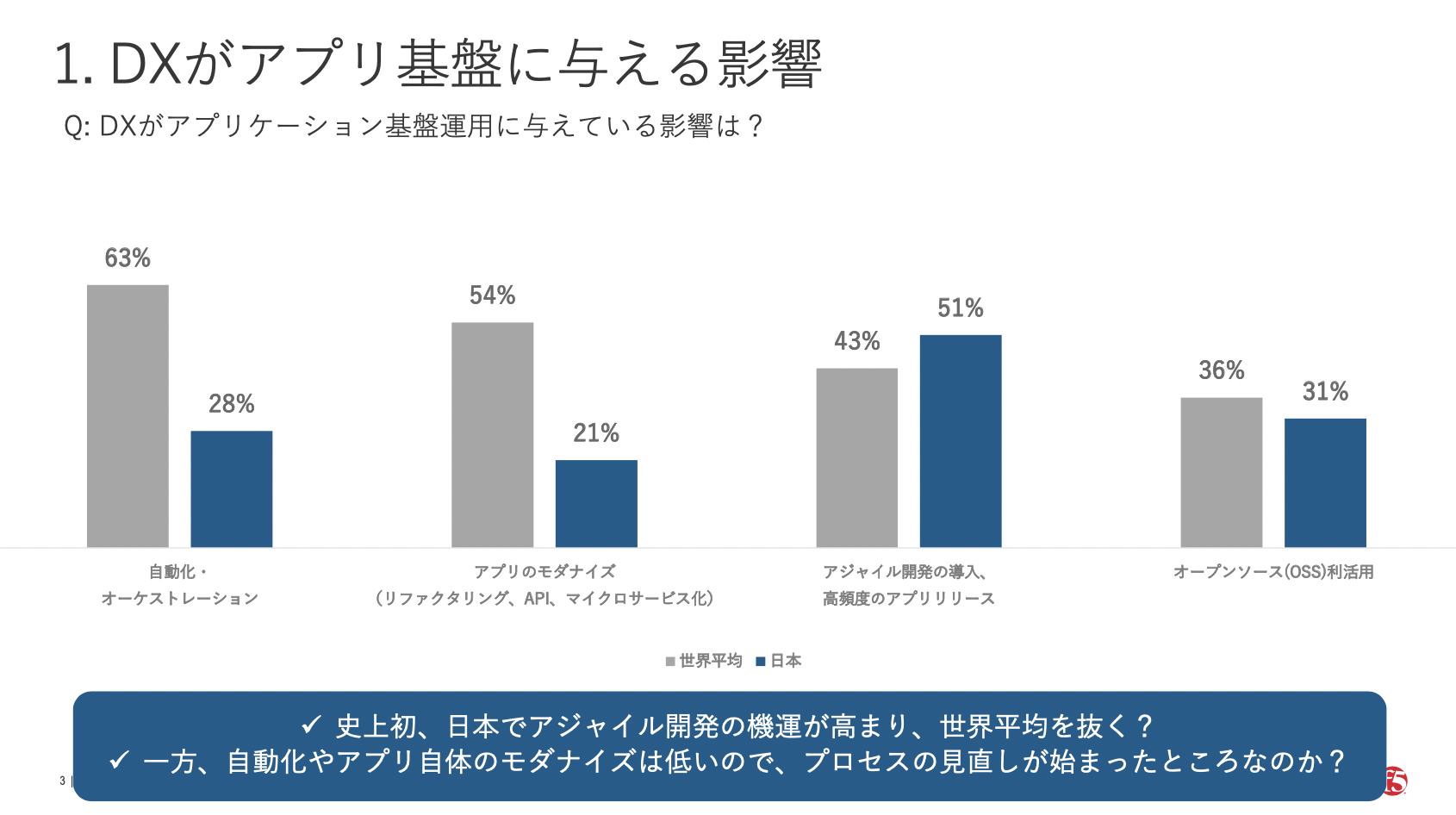
- As a shared general view, Japan’ DX development is lagging behind other countries. However, the number of Agile development is perceived as higher than the average.
- Many companies in Japan don't have CISO roles, and security is something that executives "hope" someone in the company get things done.
- That's why the assessment criteria is vague, and person in charge of cyber security don't get promoted if they are actually "successful" in their job (I think we also talked about it before as one of the pains of CISO )
- So SANS institute offers the training for companies to raise the awareness and restructure the criteria for cyber security.
- Many security experts are struggling with finding the solution which is hard for hackers but easy for users.
To sum up the whole discussion, we can break them down into 2 topics.
- Cybersecurity talent problem Companies with CISO role generally have objective metrics to assess their achievement. However this is often lack in cooperates that don't value cyber security as a professional expertise. Due to this reason, people are not attracted to be positioned in cyber security. On the other hand, there is a big market for training programs.
- Security vs Usability Robustness of security and easy usability are 2 sides on the same coin. Security is all about daily habit, and it will not make sense if the users don't use the tools for its complicated UI/UX.
How Consento works on Security vs Usability issue: The real Key is "Trust", not the Long Passwords#
In cyber security world, we often hear that "Human factor is the weakest link in chain" as in human error is the most potential danger to break the system. No matter how beautiful security tool you have, people need to have the ability to handle it right. As is discussed in the event, that is why security training is very crucial today.
As a software company, we wanted to build a tool that have the warmth of human, and we rather prefer to state "Human factors are the strongest link in chain" that can enhance the security.
Consento uses its unique authentication called "Human Factor Authentication" that requires trust from your trusted peers like friends, family, colleagues etc. On your mobile phone, you can add your "trustees" via QR code, and they act as your decentralized partial keys.
This Human Factor Authentication intends to foster the learning of trust rather than learning to manage long passwords. In Consento app, users are nudges to maintain their relations and a high level of security in their circle of devices by sending and receiving push notifications triggered by the users in the trusted circle. This sense of collaborative security gives a peace of mind with warmth of human. We don't have to do everything alone.
Humans are the creature to forget things, and learning a long sequence of passwords on each different platform is unrealistic, especially in the era of cross-using multiple platforms. Our amazing UI/UX designer Marc posted a very important quote on trust.
We like the definition of trust as "a psychological state comprising the intention to accept vulnerability based on positive expectations of the intentions or behaviour of another"(Rousseau et al., 1998). Trust depends both on the individual abilities to trust and on the trustworthiness another is able to display.
Said otherwise, trust is neither a cognitive process nor an innate human feature, it is both (Mújdricza, 2019). Studies have shown that trust is an a priori given human faculty, and therefore the possibility of trust is always present. But visual cues, human contexts and past experiences affect positively or negatively the level of trust. Trust happens to be 'learned' more than 'earned', and it requires a certain affective warmth for a start. (In consent we trust - Consento )
Trust is something to be learned, and what we want to create is not a software that just makes life easy. We want to create the software that makes people as people, and this is leading to our motto "Data privacy for humans by human." What we should learn as human is trust, not the long password.
