CISOs Interview: 3 Common Problems in Cyber Security Today

When it comes to cyber security, employees tend to think that “tech people” who know everything will take care of it with a magic wand, and it will be all well. But, is it really true?#
In an organisation, usually CISO (Chief Information Security Officer) is the role responsible for ensuring the adequate security measures for the company to protect the data assets.
Through a dozen of interviews with CISOs, we found out there are 3 common problems and challenges they think of in today’s cyber security and in their role.
1. The CISO’s role is not only to tell the bad news#
CISOs acknowledge that their role inside the organisation is often associated with telling about cyber threats, data breaches, missing security hygiene and so on. This ‘bad cop’ figure makes it difficult for CISOs to fulfill an important part of their job, which lies beyond requirement design for security technologies and protocols. Indeed, the value CISOs bring acting as a leader to onboard the workforce onto a collective digital security journey.
A hidden fact about CISO’s role is that they need to execute the emotional intelligence to educate employees about the value of data, and the way to protect their assets = organisation’s assets.
2. Expectations of velocity vs tested security#
The rapid transition to work from home (WFH) has fast paced the ongoing digital transformation of organisations. One of the CISOs we interviewed says "Making sure that we are doing the right things from a digital transformation standpoint is pretty big. A lot of businesses have done months or years worth of transformation in weeks.The biggest thing impacting right now is keeping up with digital transformation."
The apparent results may give the impression that radical changes toward digital practices can be taken collectively and in a short time. The new normal is that CEOs now expect the same velocity for digital transformation projects. However, CISOs know that healthy and secure transformation in the long term requires time to assess security and changes in security measures in the long run.
3. Digital tools (and practices) integration is pivotal, yet never achieved.#
It has become extremely demanding to find ways to integrate digital tools and practices across the organisation, at the office, on the field or at home, and beyond with the network of suppliers or partners. This task is a never ending task, dealing with the inherent multiplicity of situations while reducing risks of mis-integration.
“The area of concern for me is how to make it easy for everyone to have dual factor, but harder for the attacker to exploit which are 2 different polarizing situations.” -- Flavio Aggio, CISO at WHO
One of the factors which makes tool integration difficult is communication across organizations. Every company has different security measures and uses different tools. Upon sharing the data, we must ensure that the other party uses the tool that is compatible for both parties. The problem all comes down to how to share data securely across organizations.
Flavio Aggio, CISO at WHO says, “The area of concern for me is how to make it easy for everyone to have dual factor, but harder for the attacker to exploit which are 2 different polarizing situations.”
An organization like the World Health Organization,they have to deploy people globally in places where the supply chain is difficult. He says “sending physical MFA tokens to the right people is a major challenge where wars are going on, and really doesn’t work, so we shifted to virtual tokens in smartphones. The cost of smartphone production has been reduced, and everybody by default may have a smartphone but not a computer.”
How to turn your smartphone a secure key#
Given those 3 problems, here is the solution we have developed.
1. Intuitive, collaborative and Human-centric solution#
CISO as a role responsible for assessing the right security measures and also getting employees onboard for the security practice, collaborative security practice makes it easier for people to be a part of the game.
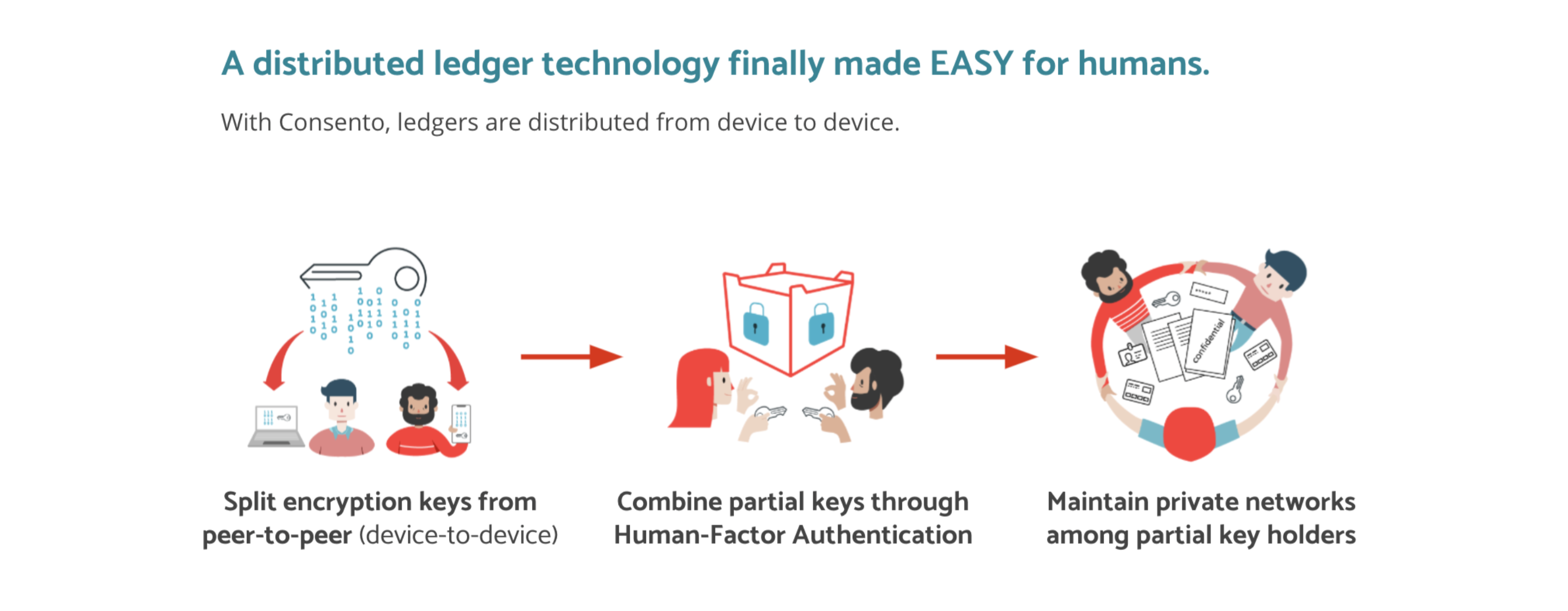
With Consento, the app split the keys partially to your trusted people which you can add as “trustees”. Upon opening a data vault, the app sends the notification to your trustees. If 3 out of your 5 trustees agreed, you can access the data with having your master key.
2. We say 3 No! No Password, No Server, No single point of failure#
Consento is backed by decentralized ledger technology which is called “Hyper Core”, and this enables the strong encryption upon devices instantly. Our P2P protocol doesn’t require servers, and there’s no single point of failure. It’s an Open Source Project that ensures full transparency. We don’t hide anything, but are very good at hiding your valuable data.
3. Easy implementation, but hard for hackers to attack#
As we know tool integration is one of the challenges CISOs often mention, we make it simple. All you need is just a smartphone, and you can add trustees with a quick QR code scanning. The implementation is super easy. In addition to that, the more you add trustees, the more it becomes secure as well. We make humans as a factor to enhance the security by our collaborative access control .
what's next#
If you are a CISO, do you resonate with any of these 3 problems? If you are not a security expert, what would you expect security experts do for you?
Please let us know! And if you want a demo of Consento technologies, get in touch with us.
