Shifting to remote working propelled the digital transformation. At what security costs?

Great! Thanks to the rapid move to #WorkFromHome, your organisation embraced #DX. But wait. At what security costs?#
As we recently shared, the recent move to work remotely came with a drastic increase in organisations' security threats. And our interviews with CISOs gave us better idea how it feels to be on the front line.
Expectations of velocity versus tested security.#
The rapid transition to work from home (#WFH) has fast paced the ongoing digital transformation (DX) of organisations of all sizes. The apparent results may give the impression that radical changes toward digital practices can be taken in a very short time. CEOs now expect the same velocity as the "new normal" for digital transformation settles. However, a transformation that is healthy and secure in the long term requires time and patience to assess security, user behaviors and changes in security measures on the long run.
Of course the CISO’s role is not only to tell the bad news.#
CISOs acknowledge that their role inside organisations is often associated with telling about cyber threats, data breaches, missing security hygiene, and so on. This ‘bad cop’ figure makes it harder for CISOs to fulfill an important part of their job Indeed, the role of CISOs lies beyond requirement design for security technologies and protocols; it encompasses acting as a leader to onboard the workforce onto a collective digital security journey.
Digital tools (and practices) integration is pivotal, yet never achieved.#
It has become extremely demanding to find ways to integrate digital tools and practices across the organisation, at the office, on the field or at home, and beyond with the network of suppliers or partners. This task is a never ending task, dealing with the inherent multiplicity of each users' situations while reducing risks of mis-integration of the system.
All in all, the digital transformation is a long on-going organisation project, transforming human factor threats into human factor liabilities.#
It requires leadership and coherence all the way long, to integrate technological solutions along with human (individual and collective) behaviours. The scope of CISO is set to expand.
One of most pressing issue CISOs face is still the use case of emails hacking. The distributed system requires [ message encryption ] + [ file exchange security ], regardless of the network used by users.
Consento provides 'human-centric MFA' + proper data encryption (ZeroTrust) + Security-as-a-network (collective security hygiene).#
How it would work in your organisation#
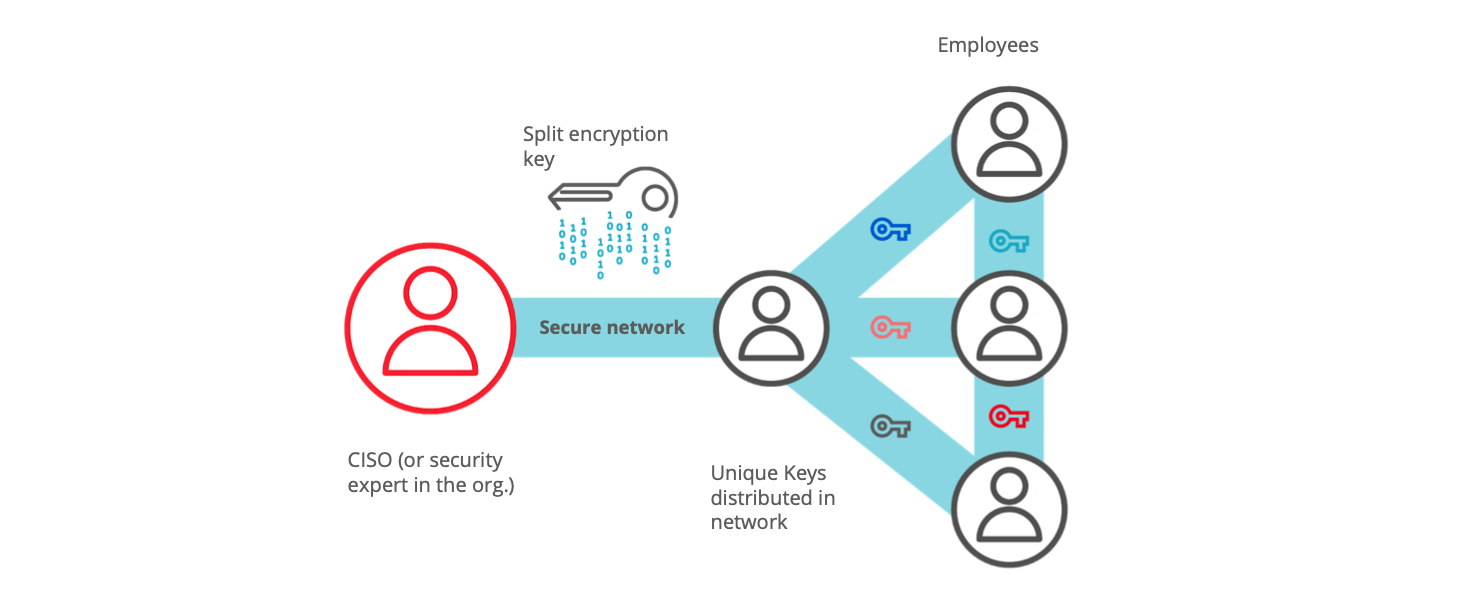
Distribute keys (digitally) easily across your organisation, in person or over a video chat.
- make sure who receives the key
- integrate easily across the organisation
- own the system (no reliance on third parties)
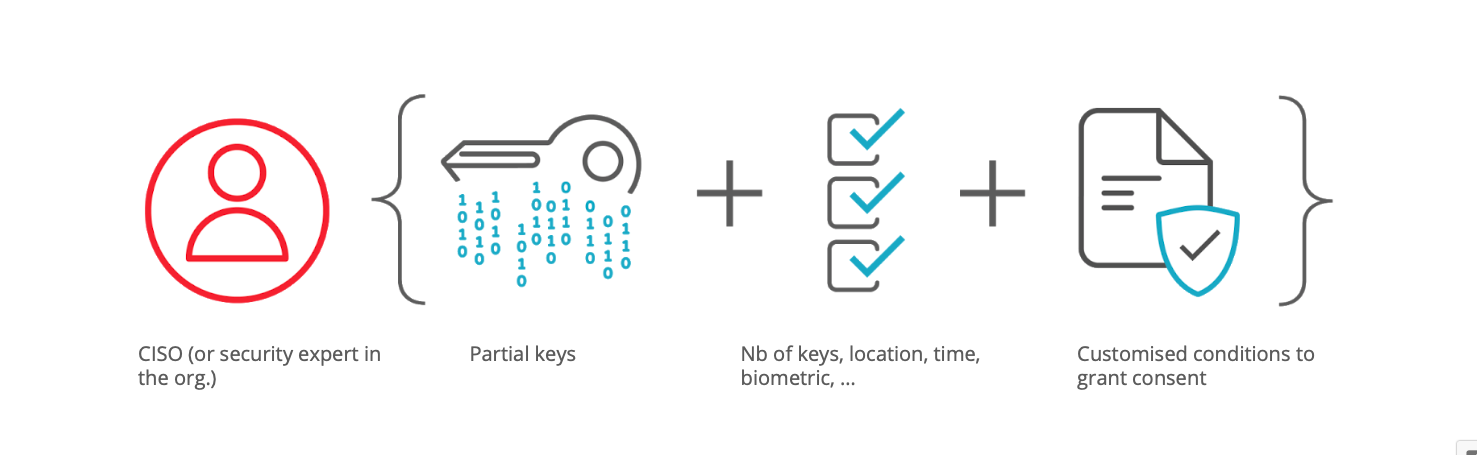
Make security your way by encrypting data and editing security conditions for consent.
- create custom MFA
- rely on password-less, SIM-less technologies
- include biometric, location or other contextual identifiers
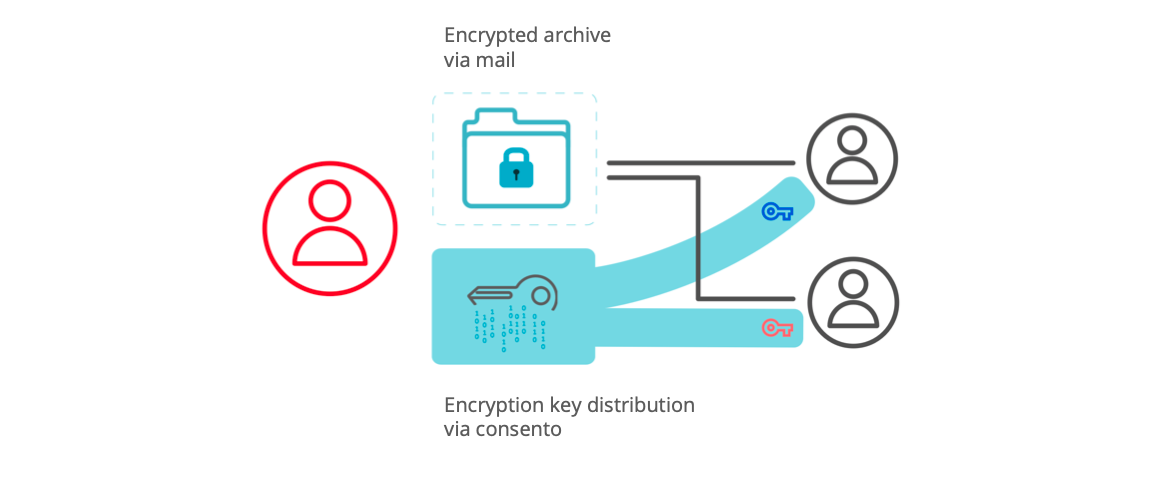
Your collaborators encrypt data locally, share the encrypted archive, and always keep the key.
- create strong encryption easily
- distribute the encrypted archive (regardless of the network) & always keep control of who can access
- add/revoke who can request access to archive
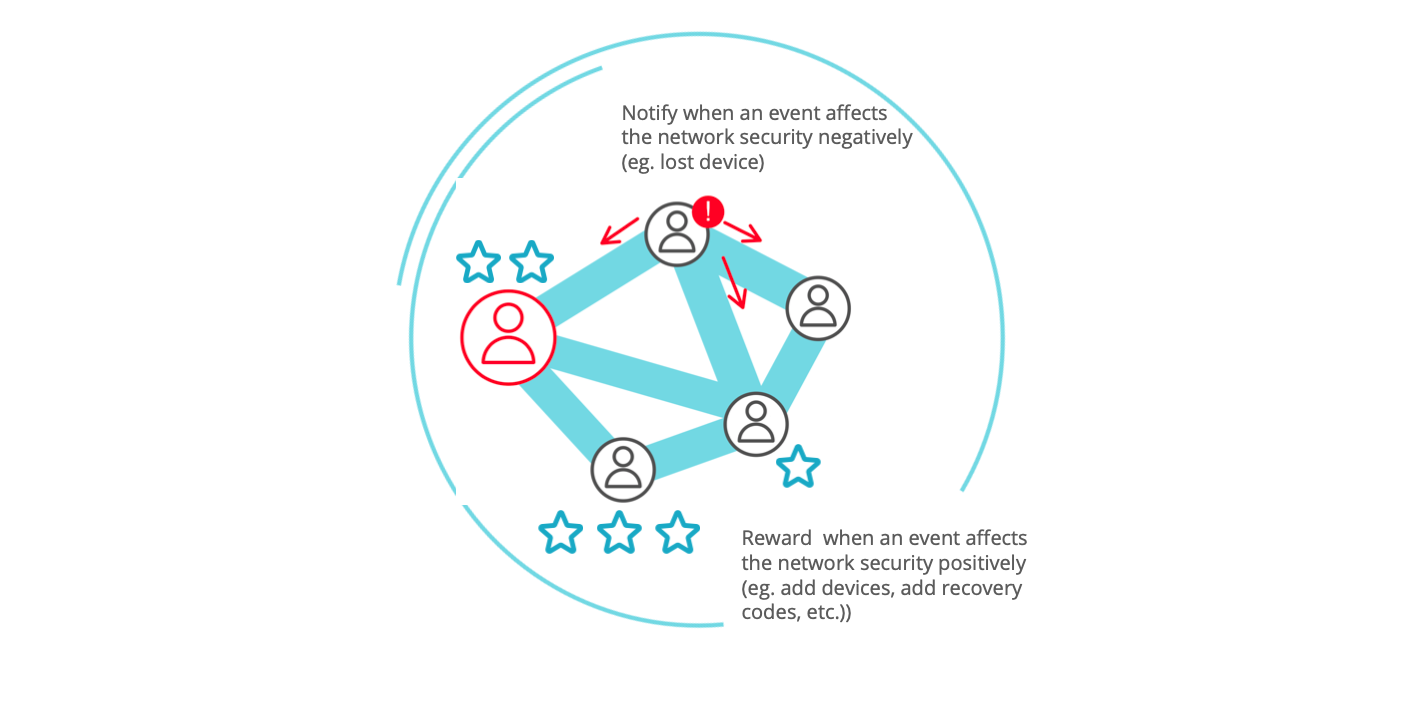
Your collaborators maintain a high security together.
- get guidance on how to keep security high
- reward collaborators (and suppliers) for their security hygiene
- nudge (or get nudged by) others in your network to nurture collective security hygiene
- keep security policies up-to-date, by notifying any event in the network affecting the collective security.
Consento provides a human-centric MFA solution to ensure the proper encryption of confidential email and file exchanges.#
The Consento app is designed to:#
- onboard all types of users as soon as they have at least one device ;
- enable them to handle MFA, SIM-free, multi-device, biometric approval ;
- onboard users across organisation(s) ;
- and nudge them to maintain a long-lasting digital security hygiene as a collective.
To wrap up, with Consento now you can:#
- delineate clear liabilities of all participants: Consento splits the encryption keys into unique partial keys.
- rely on mobile devices, SIM-free: distributed on the selected devices of the setup.
- customise your MFA with biometric authentication, geolocation or other custom parameters: Consento recomposes the secret through a Human-Factor Authentication.
- benefit from a cost-effective integration: Consento is made simple to integrate with your technical infrastructure and workforce practices.
